eBPF-for-Ghidra
The extension implements eBPF architecture support for Ghidra and allows for disassembly and decompilation of eBPF programs.
Warning: eBPF is included in Ghidra since Ghidra 10.3
Since May 2023, eBPF-for-Ghidra has been included in the official NationalSecurityAgency/Ghidra repository.
You can get the latest updates and fixes for the eBPF module directly in Ghidra.
This repo may be archived in the future.
Examples
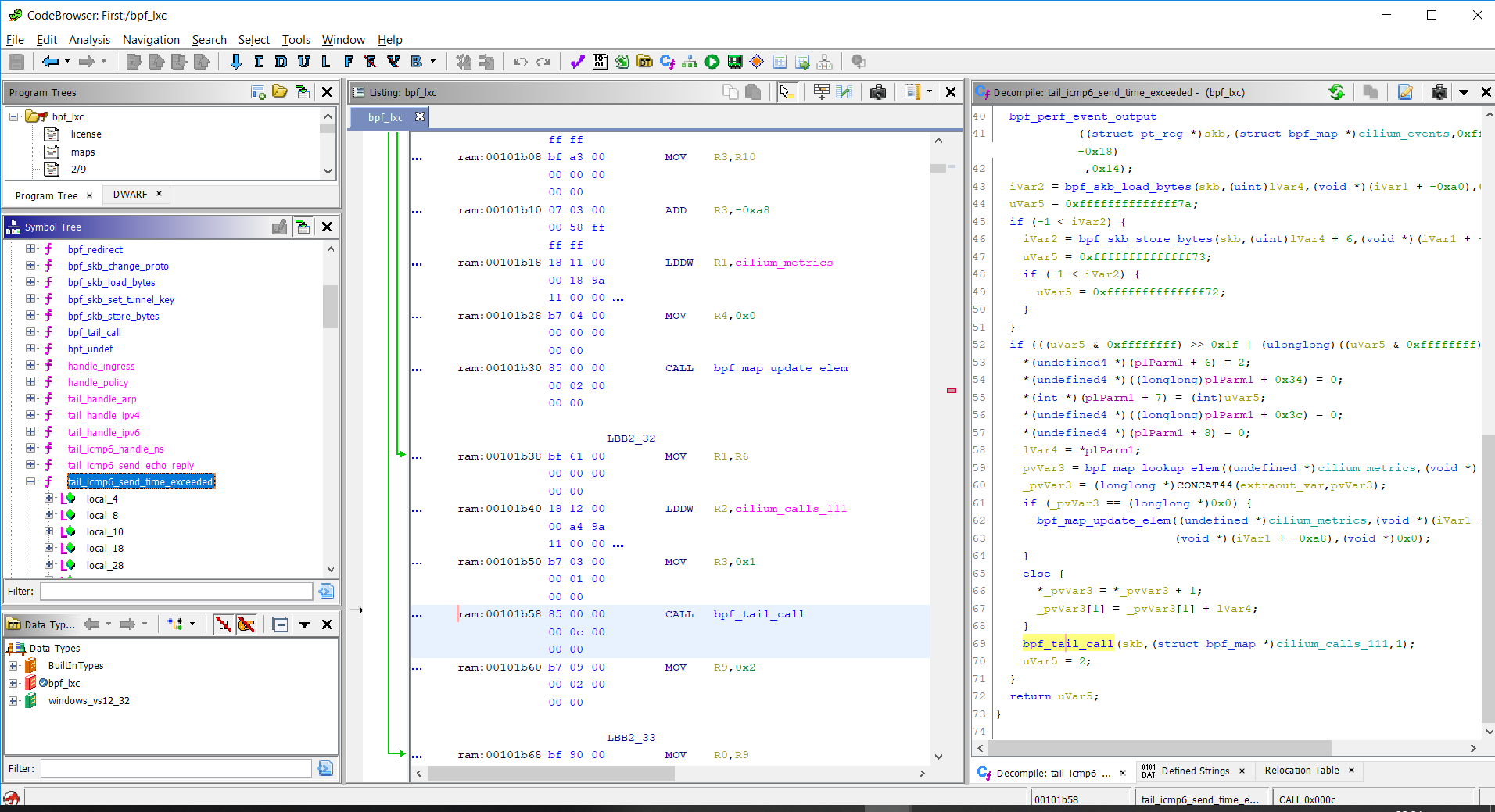
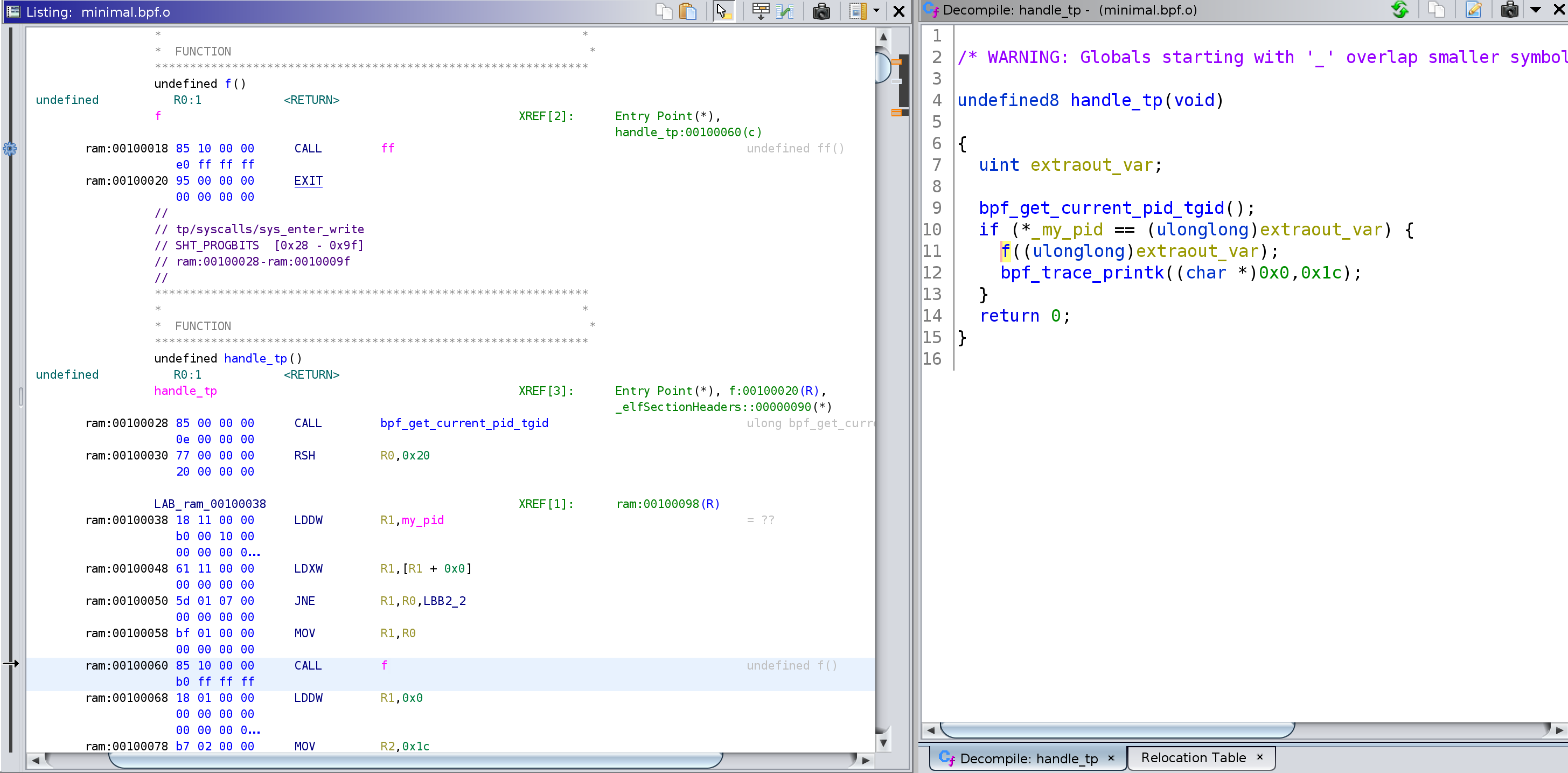
Example of eBPF program you can get here.
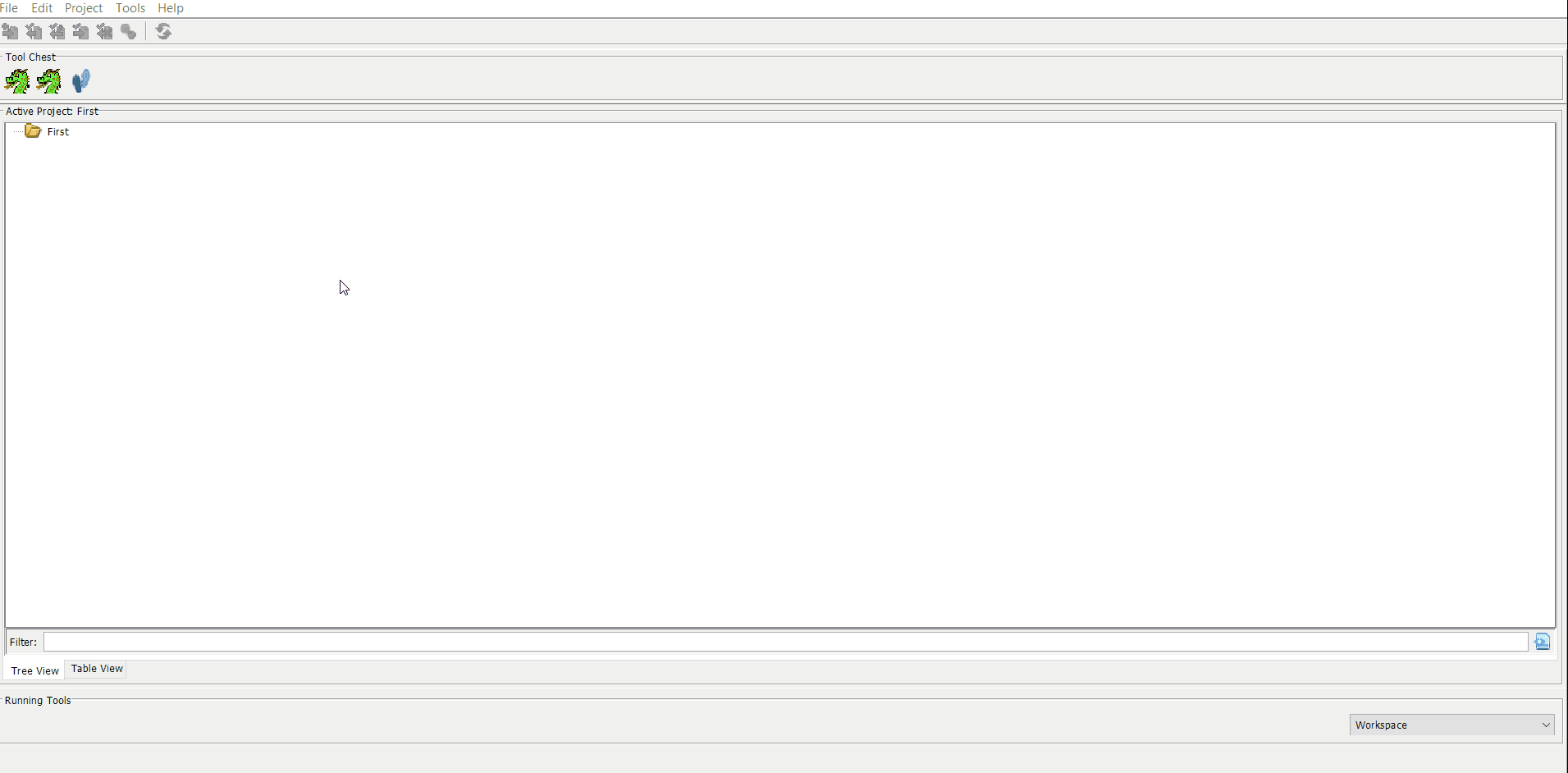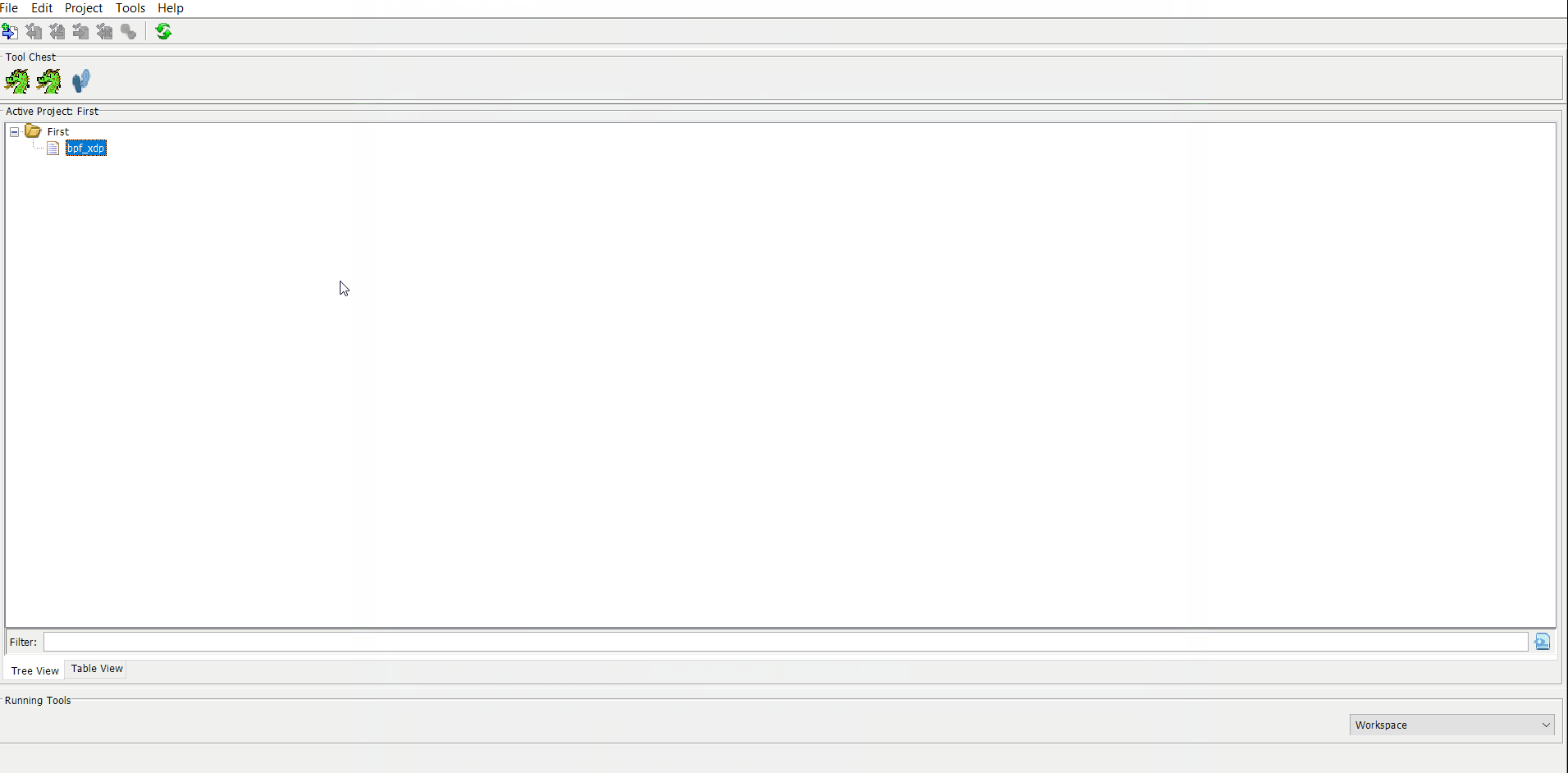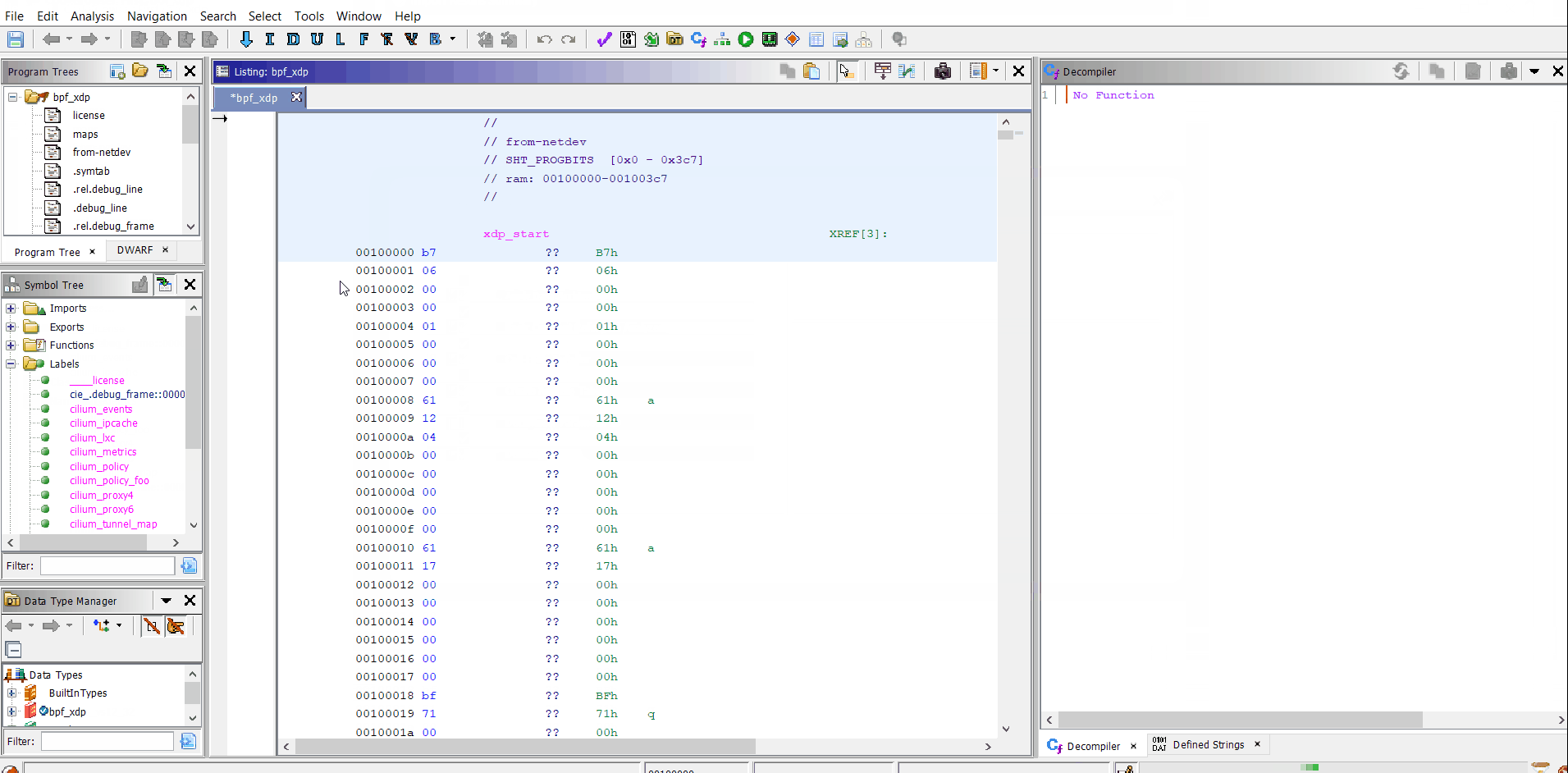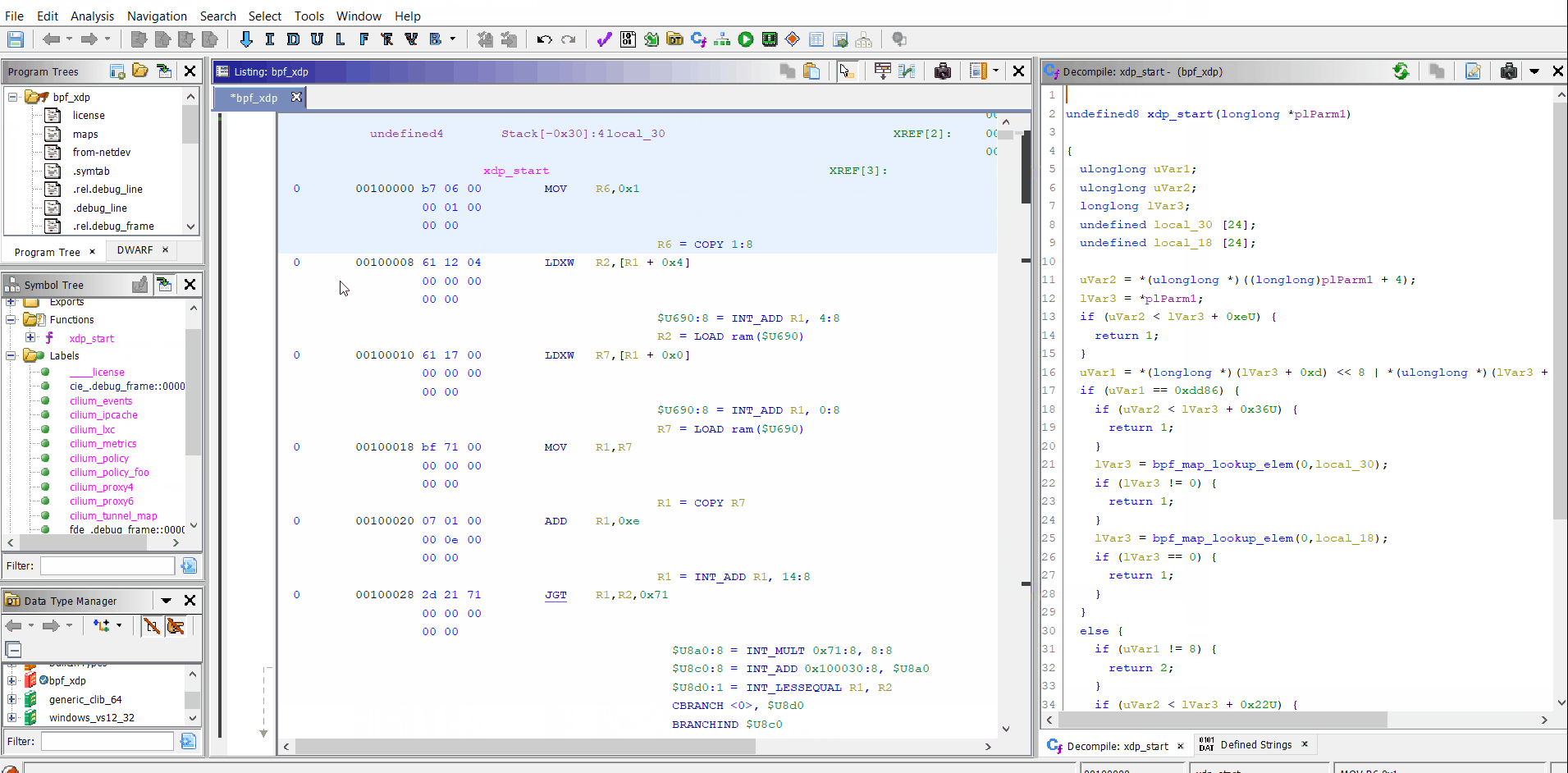
Example of disassembling and decompiling of eBPF:
Installation
- Download Release version of extension and install it in Ghidra
File → Install Extensions... - Use gradle to build extension:
GHIDRA_INSTALL_DIR=${GHIDRA_HOME} gradleand use Ghidra to install it:File → Install Extensions... - Clone this repository to
\Ghidra\Extensionsdirectory.
Updates
03.09.2019 — eBPF maps implementation, custom relocation handler was implemented
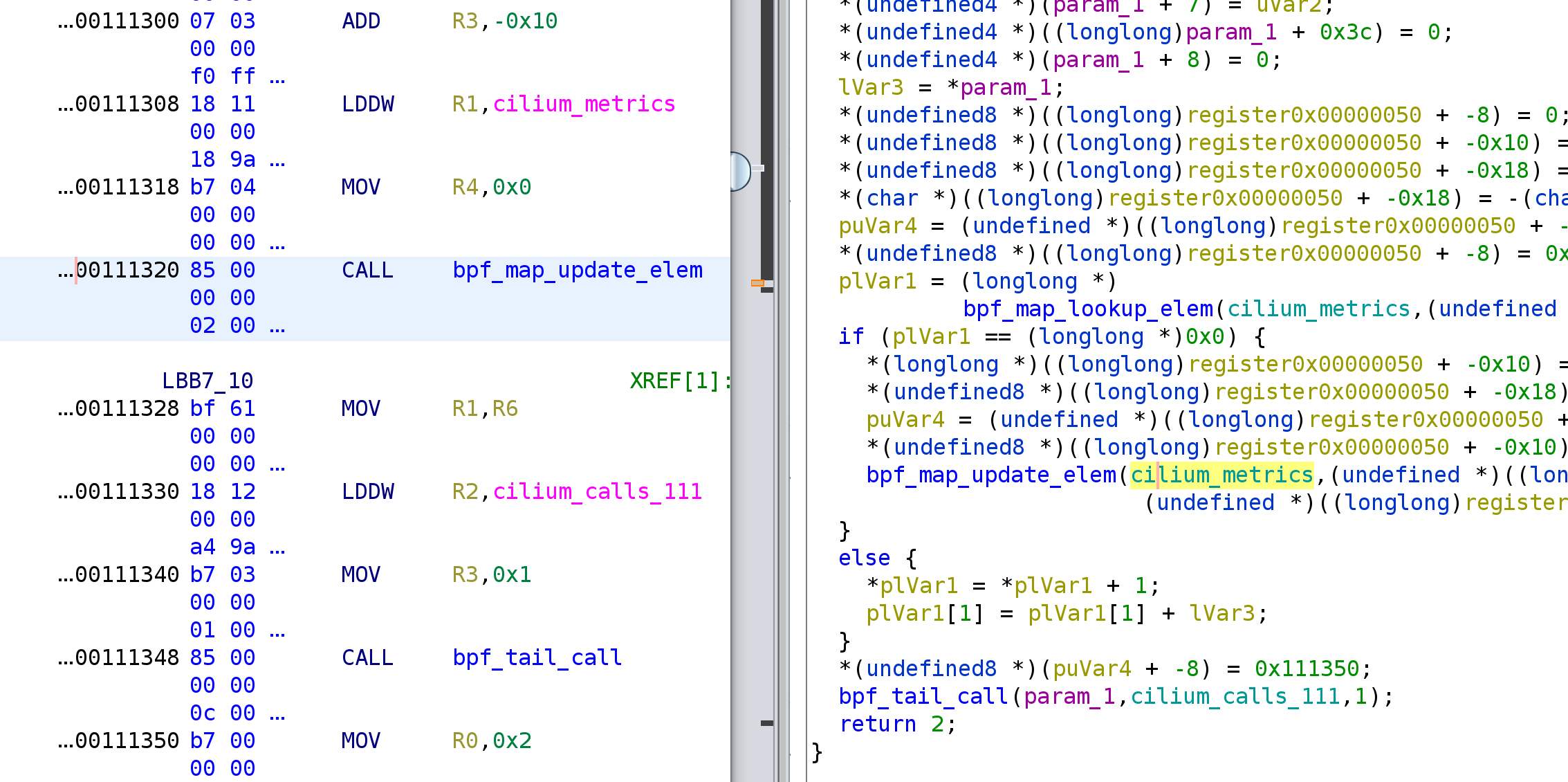
19.09.2019 — problem with stack is resolved
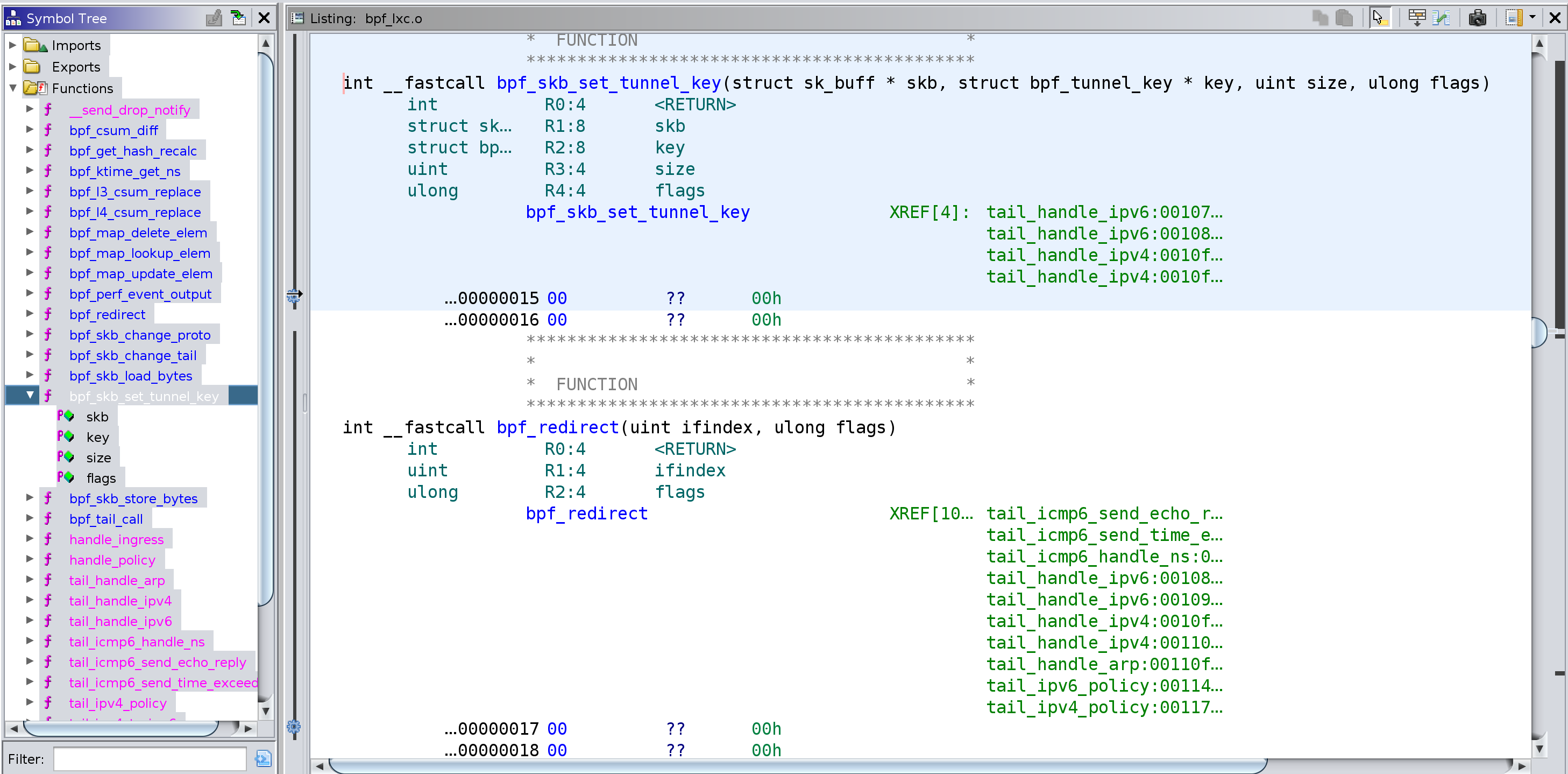
20.09.2019 — eBPF call-helpers are implemented as syscalls, added helper's signature through custom eBPFAnalyzer
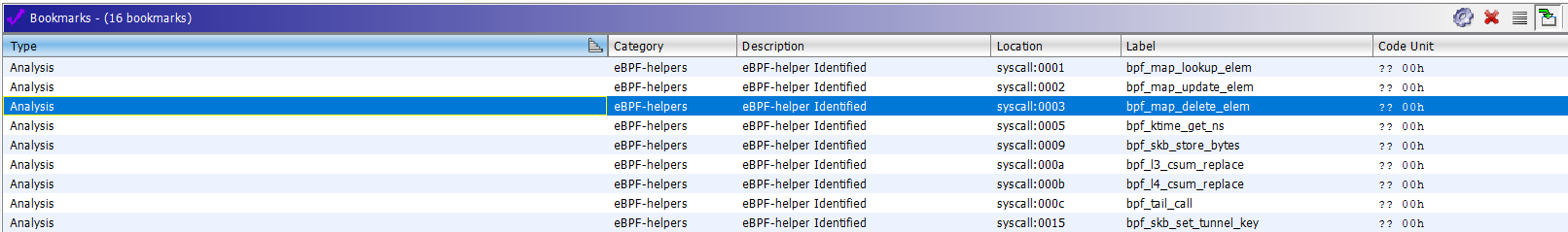
23.09.2019 — bad bookmarks fixed
01.12.2020 — new eBPF-helpers added
23.06.2022 — added support for relative calls (R_BPF_64_32 relocation type). Thanks @cnwangjihe for this idea. imm of call instruction where bpf_call->src_reg == BPF_PSEUDO_CALL now contains the relative offset to target function.
Before:

After:
24.06.2022 — making the Pull Request to official Ghidra repository as the main supplier of the eBPF processor
19.12.2022 — added support for BPF_ATOMIC operations, ALU32 instructions added, BPF_JMP32 instructions added, JSET instruction fixed
03.05.2023 — eBPF processor support added to the Ghidra official repository in the commit 506ca1e
Starting from Ghidra 10.3, the eBPF module is included by default in Ghidra. There's no need to build this project and add it as a Ghidra extension anymore. For users of older versions of Ghidra, the eBPF module can still be accessed through existing Releases.
